This article compares the top 10 incident response software solutions for 2024, covering their key features, strengths, weaknesses, deployment options, pricing, and user reviews. The goal is to help you choose the best tool for your organization's cybersecurity and incident response needs.
Related video from YouTube
Top 10 Incident Response Software
- Velociraptor: Open-source tool for endpoint monitoring, digital forensics, and cyber response. Collects forensic evidence from multiple endpoints, searches for suspicious activities, and stores events centrally.
- Cyber Triage: Helps collect and analyze data after an alert. Offers malware detection, memory analysis, artifact collection, artifact scoring, and integration with SIEM and SOAR systems.
- CrowdStrike Falcon: Detects, responds to, and fixes cyber threats. Provides NGAV, EDR, intelligence-led incident response, threat hunting, and forensic artifact capture.
- Palo Alto Networks DFIR: Global service for quick threat understanding and action. Integrates with Cortex XDR, Xpanse, and Prisma Cloud for immediate response.
- FTK Forensics Toolkit: Digital forensics tool for retrieving data from encrypted drives, analyzing mobile data, and evaluating visual evidence.
- SIFT Workstation: Free, open-source toolset for incident response and digital forensics. Includes tools for disk imaging, file system analysis, and data recovery.
- Sprinto: Helps businesses meet compliance standards like SOC 2, ISO 27001, and GDPR. Offers automated evidence collection, compliance monitoring, and risk assessment tools.
- IBM Security QRadar SIEM: Provides real-time visibility into IT infrastructure. Uses analytics, machine learning, and threat intelligence for threat detection and prioritization.
- Symantec Endpoint Security: Protects laptops, desktops, and file servers from online threats. Includes antivirus, antispyware, and a firewall.
- Webroot Business Endpoint Protection: Cloud-based security solution for businesses. Offers real-time threat detection, automated threat protection, and customizable policies.
Quick Comparison
| Software | Key Features | Strengths | Weaknesses | Pricing | Deployment Options |
|---|---|---|---|---|---|
| Velociraptor | Endpoint monitoring, digital forensics, cyber response | Precise threat hunting, effective for large deployments | Requires forensics knowledge, may not scale well for very large deployments | Open-source | Windows, Linux, Mac |
| Cyber Triage | Malware detection, memory analysis, artifact collection | Fast and thorough, integrates with SIEM/SOAR | May need extra training, limited compared to general forensics tools | $1,999/year/user | On-premise, cloud |
| CrowdStrike Falcon | NGAV, EDR, incident response, threat hunting | Fast, effective, intelligence-led | May need extra training, resource-intensive | Premium | On-premise, cloud |
| Palo Alto Networks DFIR | Global service, integration with AI-powered solutions | Quick action, detailed investigation | - | - | Global |
| FTK Forensics Toolkit | Data recovery, digital data analysis, mobile forensics | Digital forensics solution, strong investigation tools | - | - | On-premise, cloud |
| SIFT Workstation | Disk imaging, file system analysis, data recovery | Free, open-source, live environment | - | Free | Live environment |
| Sprinto | Automated evidence collection, compliance monitoring | Real-time monitoring, risk assessment tools | - | - | - |
| IBM Security QRadar SIEM | Analytics, machine learning, threat intelligence | Advanced threat detection, user behavior analytics | - | - | - |
| Symantec Endpoint Security | Antivirus, antispyware, firewall | Centralized management, vulnerability management | - | - | - |
| Webroot Business Endpoint Protection | Real-time threat detection, automated protection | Cloud-based management, customizable policies | May require internet, limited offline capabilities | - | - |
1. Velociraptor
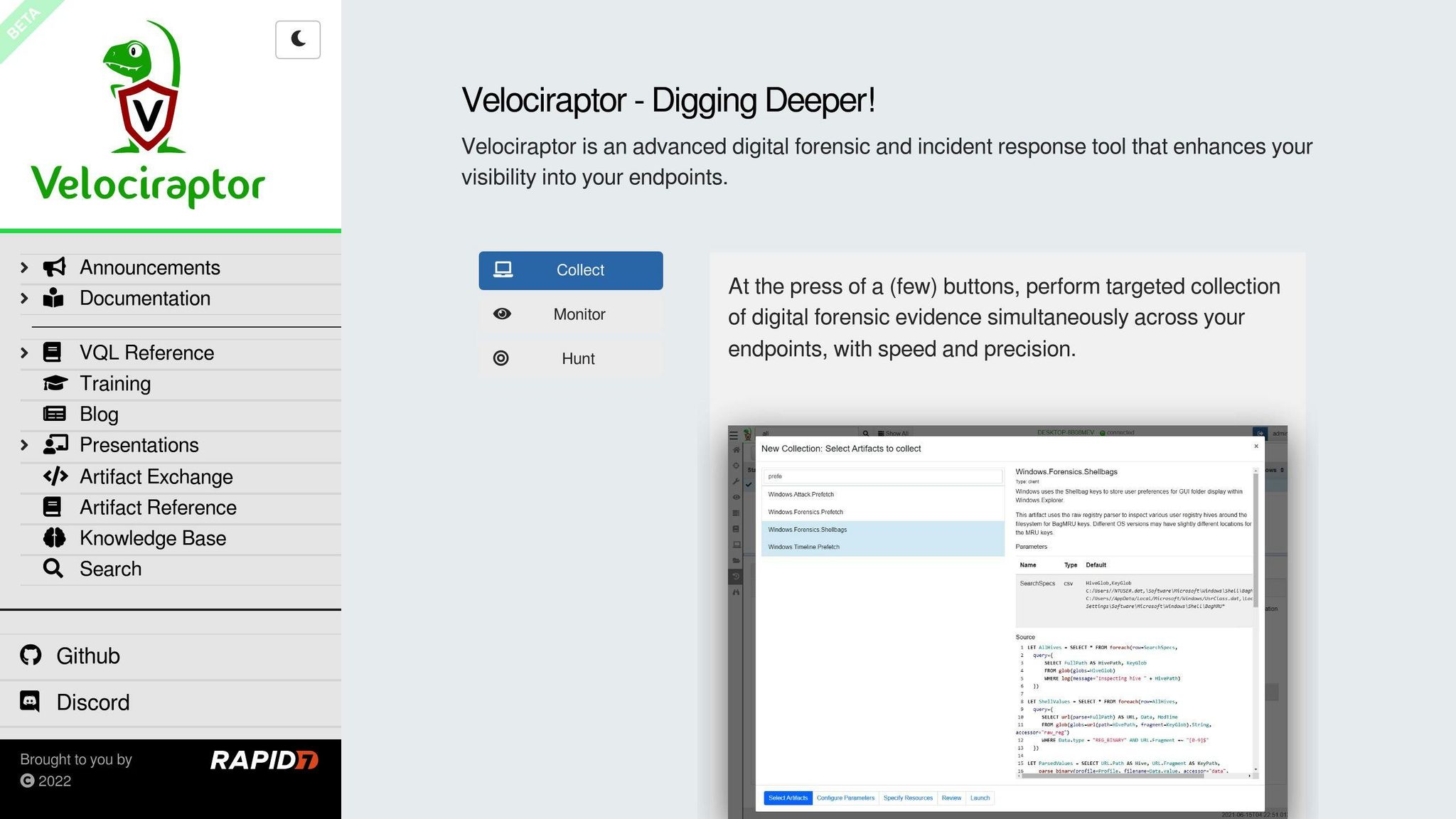
Key Features
Velociraptor is an open-source tool for endpoint monitoring, digital forensics, and cyber response. It helps in investigating data breaches and cyber incidents. Key features include:
- Collecting forensic evidence from multiple endpoints at once
- Searching for suspicious activities using a library of forensic artifacts
- Continuously collecting endpoint events like logs, file changes, and process execution
- Storing events centrally for historical review
Strengths and Weaknesses
| Strengths | Weaknesses |
|---|---|
| Provides precise threat hunting and detection | Requires knowledge of digital forensics and incident response |
| Effective for large-scale deployments | Traditional workflow may not scale well for very large deployments |
Deployment Options
Velociraptor can be installed on Windows, Linux, and Mac systems. It has an active community that contributes to its features and threat hunts.
User Reviews
Users have given positive feedback for its threat hunting and detection capabilities. Its open-source nature and community support are also well-regarded.
2. Cyber Triage
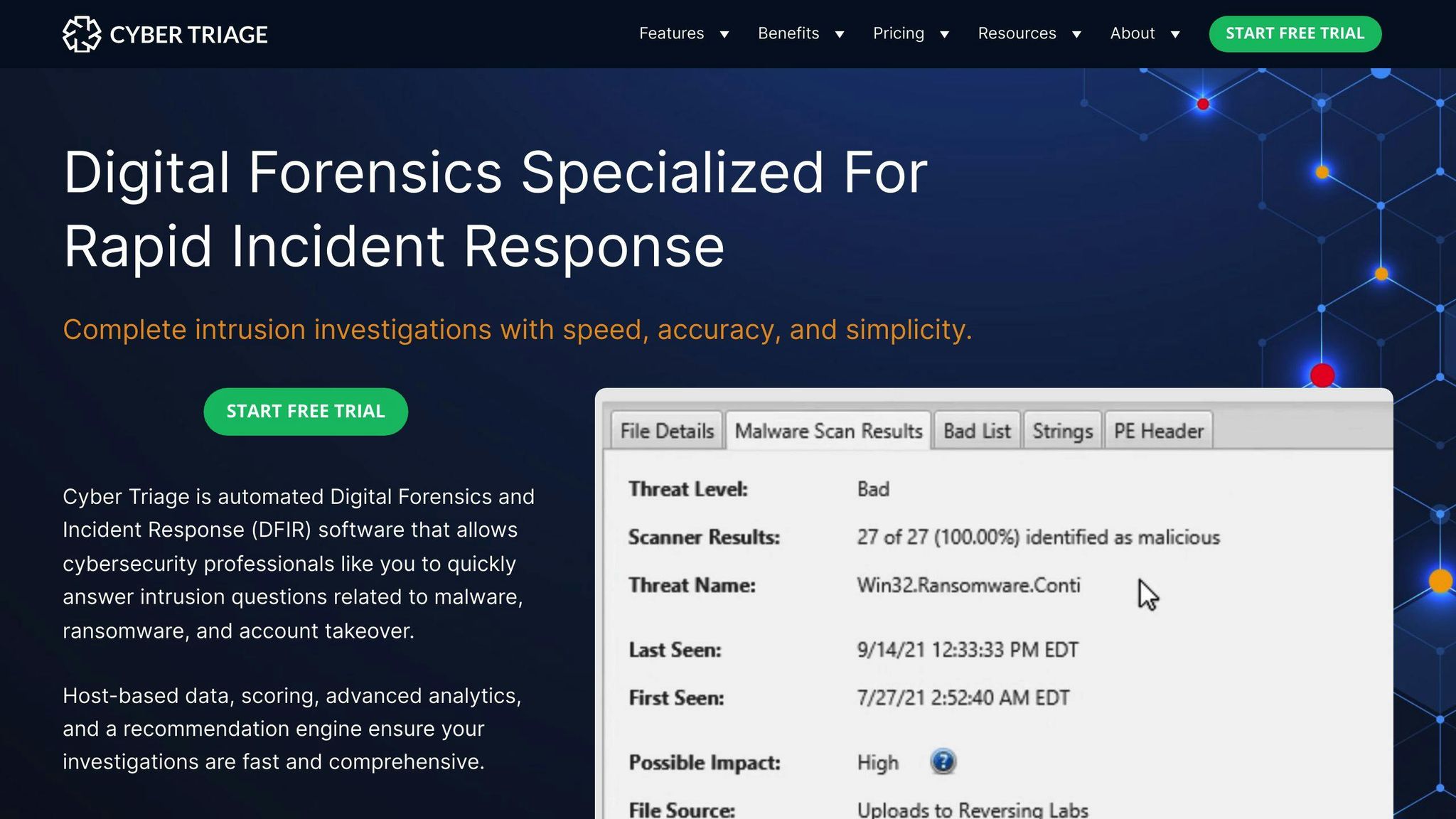
Key Features
Cyber Triage is an incident response tool that helps businesses collect and analyze data after an alert. Key features include:
- Malware detection and analysis
- Memory image analysis
- Yara rules integration
- Threat timeline analysis
- Multi-user database
- JSON reporting
- Headless ingest
- Artifact collection (volatile data, malware persistence, user activity)
- Scoring and prioritization of artifacts based on risk
- Integration with SIEM and SOAR systems
Strengths and Weaknesses
| Strengths | Weaknesses |
|---|---|
| Fast and thorough digital forensics and incident response | May need extra training for effective use |
| Efficient incident response | Limited compared to general-purpose forensics tools |
| Integrates with SIEM and IDS for automated collections | |
| Automated analysis and artifact correlation | |
| Quick communication of results | |
| Detailed artifact scoring and prioritization |
Pricing
Cyber Triage pricing starts at $1,999 per year per user.
Deployment Options
Cyber Triage is suitable for all sizes of organizations, from small businesses to large enterprises. It can be deployed on-premise or in the cloud.
User Reviews
Users appreciate Cyber Triage for its speed, thoroughness, and ease of use in incident response and digital forensics. Its integration with SIEM and SOAR systems is also a key strength.
3. CrowdStrike Falcon
Key Features
CrowdStrike Falcon helps organizations detect, respond to, and fix cyber threats. Key features include:
- Next-generation antivirus (NGAV) and endpoint detection and response (EDR)
- Intelligence-led incident response and remediation
- Real-time threat hunting and response
- Automated data collection and enrichment
- Advanced query capabilities for Tier III threat hunting
- Forensic artifact capture, including MFT, shimcache, shellbags, and others
- Large-scale deployment capabilities
Strengths and Weaknesses
| Strengths | Weaknesses |
|---|---|
| Fast and effective in responding to incidents | May need extra training for effective use |
| Intelligence-led investigation and remediation | Can be resource-intensive |
| Tailored approach to incident response | |
| Tools and technology for improved security posture | |
| Managed threat hunting services |
Pricing
CrowdStrike Falcon pricing is not publicly disclosed but is generally considered a premium solution.
Deployment Options
CrowdStrike Falcon is suitable for organizations of all sizes, from small businesses to large enterprises. It can be deployed on-premise or in the cloud.
User Reviews
Users praise CrowdStrike Falcon for its speed, effectiveness, and intelligence-led approach to incident response and remediation. Its managed threat hunting services are also a key strength.
4. Palo Alto Networks DFIR
Key Features
Palo Alto Networks' Digital Forensics and Incident Response (DFIR) service helps organizations quickly understand and respond to threats. Key features include:
- Global DFIR service for quick threat understanding and action
- Integration with Cortex XDR, Xpanse, and Prisma Cloud for immediate response
- Detailed investigation using Palo Alto Networks' security expertise
- Contextual threat response using a dataset of over 500 billion daily events
Strengths
| Strengths |
|---|
| Global service for quick action against threats |
| Integration with AI-powered solutions for immediate response |
| Detailed investigation using security expertise |
| Contextual threat response using a large dataset |
Pricing
Palo Alto Networks' DFIR pricing is not publicly disclosed.
Deployment Options
Palo Alto Networks' DFIR is suitable for all sizes of organizations. It can be deployed globally.
User Reviews
Users praise Palo Alto Networks' DFIR for its quick action against threats and detailed investigations.
sbb-itb-d1a6c90
5. FTK Forensics Toolkit
FTK Forensics Toolkit is a digital forensics tool that helps investigators find critical evidence quickly. It offers a range of tools to analyze data from various sources like email archives, mobile devices, and internet storage.
Key Features
- Advanced Data Recovery: Retrieve data from encrypted drives or deleted files.
- Digital Data Analysis: Handle large volumes of digital evidence.
- Mobile and Database Forensics: Extract and analyze mobile data and databases.
- Video and Image Analysis: Evaluate visual evidence thoroughly.
- DFIR Integration: Work seamlessly with other digital forensics and incident response tools.
Strengths
| Strengths |
|---|
| Digital forensics solution |
| Strong investigation tools |
| Easy-to-use interface |
| Advanced data recovery |
| Handles large data volumes |
Pricing
FTK Forensics Toolkit pricing is not publicly disclosed.
Deployment Options
FTK Forensics Toolkit can be used by organizations of all sizes and can be deployed on-premises or in the cloud.
User Reviews
Users praise FTK Forensics Toolkit for its features, strong investigation tools, and user-friendly interface.
6. SIFT Workstation
SIFT Workstation is a free, open-source toolset for incident response and digital forensics. It offers a range of tools for detailed forensic examinations.
Key Features
- Customized Linux Distribution: Built on Ubuntu Linux with pre-installed tools for forensics and incident response.
- Live Environment: Can be run from a USB drive, DVD, or network boot without installation.
- Forensic Mode: Ensures the integrity of digital evidence by preventing changes to data.
- Comprehensive Toolkit: Includes tools for disk imaging, file system analysis, memory analysis, registry analysis, data recovery, and network analysis.
Strengths
| Strengths |
|---|
| Free and open-source |
| Customized Linux distribution |
| Live environment |
| Forensic mode |
| Comprehensive toolkit |
User Reviews
Users praise SIFT Workstation for its wide range of tools, ease of use, and customization options. It has over 125,000 downloads, making it a popular choice for incident response and digital forensics.
7. Sprinto
Sprinto is a platform for managing compliance and security, helping businesses meet standards like SOC 2, ISO 27001, and GDPR.
Key Features
- Automated Evidence Collection: Reduces manual work by automatically gathering necessary documents.
- Real-Time Compliance Monitoring: Constantly checks compliance status and alerts users to potential issues.
- Risk Assessment Tools: Helps identify, analyze, and prioritize security risks.
- Customizable Security Policies: Allows businesses to tailor security policies to their needs.
- Integration with Existing Tools: Works with various business tools like project management software and cloud storage.
Strengths
| Strengths |
|---|
| Automated evidence collection |
| Real-time compliance monitoring |
| Risk assessment tools |
| Customizable security policies |
| Integration with existing tools |
User Reviews
Users praise Sprinto for its features, ease of use, and support. It simplifies the compliance process and reduces the workload of maintaining compliance.
8. IBM Security QRadar SIEM
IBM Security QRadar SIEM provides real-time visibility into your IT infrastructure. It uses advanced analytics, machine learning, and threat intelligence to detect and prioritize security incidents.
Key Features
- Risk-based alert prioritization: Uses multiple layers of risk scoring to focus on the most important cases.
- Sigma community rules: Supports thousands of open-source Sigma Rules for quick import of new instructions.
- Threat intelligence: Integrates with security technologies for monitoring, incident analysis, and data enrichment.
- User behavior analytics: Enhances alert enrichment, threat prioritization, and incident correlation.
Strengths
| Strengths |
|---|
| Advanced analytics and machine learning |
| Real-time visibility into IT infrastructure |
| Threat intelligence and incident response |
| User behavior analytics and alert enrichment |
| Integration with various security technologies |
User Reviews
Users praise IBM Security QRadar SIEM for its advanced features, ease of use, and effective threat detection. It has an average rating of 79, with many users highlighting its quick threat detection and response capabilities.
9. Symantec Endpoint Security
Symantec Endpoint Security is a suite designed to protect laptops, desktops, and file servers from online threats. It includes antivirus, antispyware, and a firewall to guard against malware and unauthorized access.
Key Features
- Centralized Management: Set policies, receive alerts, and manage updates from a single console.
- Real-Time Monitoring: Continuously monitor devices to detect and respond to threats.
- Endpoint Detection and Response (EDR): Advanced threat detection, incident response, and investigation.
- Vulnerability Management: Identify and prioritize security vulnerabilities for proactive remediation.
Strengths
| Strengths |
|---|
| Comprehensive endpoint security |
| Centralized management and real-time monitoring |
| Advanced threat detection and incident response |
| Effective vulnerability management |
User Reviews
Symantec Endpoint Security has positive reviews for its ease of use, effective threat detection, and robust features. It has an average rating of 4.4 out of 5, with users highlighting its strong protection for endpoint devices.
10. Webroot Business Endpoint Protection
Webroot Business Endpoint Protection is a cloud-based security solution for businesses of all sizes. It offers a single management console for admins to monitor and control all endpoints within a network.
Key Features
- Real-Time Threat Detection: Continuously monitors endpoints to detect and protect against threats.
- Cloud-Based Management: No need for on-premises hardware or software.
- Automated Threat Protection: Includes malware detection, ransomware protection, and phishing defense.
- Customizable Policies: Admins can create policies to fit their organization's needs.
Strengths and Weaknesses
| Strengths | Weaknesses |
|---|---|
| Real-time threat detection | May require internet connectivity for full functionality |
| Cloud-based management | Limited offline capabilities |
| Automated threat protection | Some advanced features may need configuration |
| Customizable policies | Initial setup can be complex |
User Reviews
Webroot Business Endpoint Protection has positive reviews for its ease of use, effective threat detection, and strong features. It has an average rating of 4.2 out of 5, with users highlighting its protection for endpoint devices.
Advantages and Drawbacks
When choosing incident response software, it's important to know the pros and cons of each tool. Here's a summary of the benefits and limitations of the top 10 incident response software:
Advantages:
- Real-time threat detection: Most tools offer real-time detection, allowing quick responses to security threats.
- Automated threat protection: Many tools automate threat protection, reducing the workload on security teams and minimizing human error.
- Customizable policies: Most software allows for policy customization, letting organizations tailor security protocols to their needs.
- Cloud-based management: Cloud-based consoles offer ease of use, scalability, and flexibility in managing incident responses.
Drawbacks:
- Complexity: Some software can be complex to set up and configure, requiring significant resources and expertise.
- Internet connectivity requirements: Cloud-based software may need internet connectivity, which can be a limitation in certain environments.
- Limited offline capabilities: Some tools may have limited offline functionality, making them less effective without internet access.
- Cost: Incident response software can be expensive, especially for smaller organizations or those with limited budgets.
| Software | Advantages | Drawbacks |
|---|---|---|
| Velociraptor | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| Cyber Triage | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| CrowdStrike Falcon | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| Palo Alto Networks DFIR | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| FTK Forensics Toolkit | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| SIFT Workstation | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| Sprinto | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| IBM Security QRadar SIEM | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| Symantec Endpoint Security | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
| Webroot Business Endpoint Protection | Real-time threat detection, automated threat protection, customizable policies, cloud-based management | Complexity, internet connectivity requirements, limited offline capabilities, cost |
Final Thoughts
Choosing the right incident response software is key for organizations to detect, investigate, and respond to security incidents effectively. The top 10 tools in this article offer features like real-time threat detection, automated threat protection, customizable policies, and cloud-based management.
However, consider the potential drawbacks:
| Drawbacks | Details |
|---|---|
| Complexity | Some software can be hard to set up and configure, needing significant resources and expertise. |
| Internet Connectivity | Cloud-based software may need internet access, which can be a limitation in certain environments. |
| Limited Offline Capabilities | Some tools may not work well without internet access. |
| Cost | Incident response software can be expensive, especially for smaller organizations or those with limited budgets. |
Organizations should evaluate their specific needs, budget, and existing security setup to choose the most suitable incident response software.
The goal is to improve an organization's security, minimize the impact of security incidents, and ensure a quick and efficient response. By using these top incident response tools, organizations can stay ahead of cyber threats and protect their critical assets.


